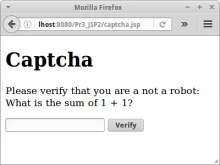
Fake CAPTCHA is part of a campaign that exposes the dark side of the internet's advertising ecosystem. It thrives by targeting social media accounts, banking information, passwords, and personal files through platforms like Facebook, Google Ads, and public repositories on GitHub. These deceptive ads have been stealing information and causing financial losses for months by hijacking advertisements and replacing them with malicious CAPTCHA pages.